Bagi pengguna Google Chrome, ada Extensions atau semacam plugins yang bisa kita tambahkan (install) untuk menyimpan halaman web secara utuh dan bisa dibaca offline (tanpa koneksi internet). Bagi pengguna web browser lain semisal Firefox, saya juga pernah mengulas untuk menyimpan halaman website menggunakan plugins Mozilla Archive Format /MAFF atau teknik lainnya (bisa dibaca Menyimpan Satu Halaman penuh Website (Firefox, Chrome, Safari) atau Tips menyimpan sebuah halaman web secara utuh).
Sebenarnya ada beberapa extension Chrome yang bisa kita gunakan, sebelumnya saya pernah menggunakan Chromium Scrapbook, dan sampai saat ini masih berjalan normal dan bisa digunakan. Sayangnya Scrapbook ini sudah dihentikan pengembangannya, meskipun masih bisa digunakan. Alternatif lain yang tidak kalah bagus adalah PageArchiver.

PageArchiver merupakah extensions Google Chrome yang mempunyai fitur mirip dengan Scrapbook, tetapi lebih lengkap. Fitur-fiturnya antara lain :
- Menyimpan halaman web (arsip) secara utuh agar bisa dibaca offline
- Export atau import file dalam bentuk HTML, sehingga bisa dibaca (pindah) secara terpisah di luar PageArchiver
- Mengedit halaman web yang sudah disimpan dengan fitur dari PageArchiver
- Menambahkan tags dan rating untuk arsip yang sudah disimpan
- Filter dengan kata tertentu untuk mencari arsip yang sudah disimpan
- Mengurutkan arsip atau halaman yang sudah disimpan berdasar tanggal, judul, url, tag dan lainnya
- Bisa melakukan pencarian melalui omnibox dengan mengetikkan ‘pa’ di alamat URL chrome
- Bookmark dan menyimpan arsip dengan Ctrl+S
Penggunaan PageArchiver
Untuk menggunakan extension ini, download PageArchiver dan install di google chrome. Sebagai catatan, extension ini memerlukan “SingleFile Core” yang juga harus di install, bisa langsung install dari halaman SingleFile Core.Setelah di install, di toolbar Google Chrome akan tampil icon seperti “open Folder” yang menunjukkan bahwa PageArchiver sudah aktif dan bisa kita gunakan. Untuk menyimpan halaman website, buka dulu halaman website yang ingin kita simpan, lalu klik icon PageArchiver dan pilih menu “tabs”. Selanjutnya kita bisa memilih tab atau artikel mana yang akan disimpan ( pilih dengan memberi tanda check dan klik tombol “save” dan tunggu proses penyimpanan selesai)

Setelah halaman website tersimpan kita bisa melihat melalui PageArchiver melalui menu atau link Archives. Tersedia beberapa menu, seperti Open (untuk membuka halaman web), Delete, Tags dan Export (untuk menyimpan arsip menjadi sebuah file html yang bisa dibuka secara terpisah).
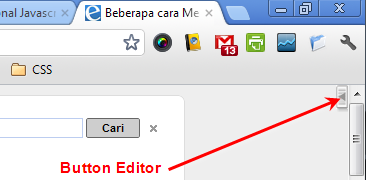
Untuk mengedit halaman website, PageArchiver juga memberikan fitur menarik. Buka halaman website dengan PAgeArchiver kemudian klik tombol yang ada di pojok kanan atau untuk menampilkan menu editor. Selanjutnya setelah kita edit halaman web ini bisa kita simpan.


Jika halaman yang kita simpan sudah banyak, kita juga bisa mencari melalui alamat URL di google chrome. Ketikkan saja kata ‘pa’ (tanpa tanda petik) dan ikuti dengan spasi, maka otomatis akan tampil “Page Archiver” dan kita bisa mencari artikel yang sudah tersimpan.
#sumber..,, http://ebsoft.web.id/simpan-halaman-web-untuk-dibaca-offline-google-chrome/